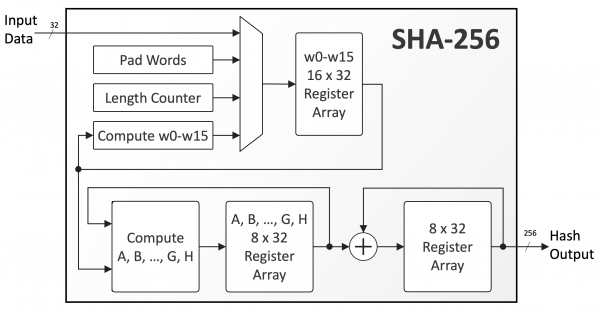
![PDF] An ASIC design for a high speed implementation of the hash function SHA -256 (384, 512) | Semantic Scholar PDF] An ASIC design for a high speed implementation of the hash function SHA -256 (384, 512) | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/60b9bb5952c3870d2f074d0c79a5e0cdd13f1924/2-Figure1-1.png)
PDF] An ASIC design for a high speed implementation of the hash function SHA -256 (384, 512) | Semantic Scholar
![PDF] An ASIC design for a high speed implementation of the hash function SHA -256 (384, 512) | Semantic Scholar PDF] An ASIC design for a high speed implementation of the hash function SHA -256 (384, 512) | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/60b9bb5952c3870d2f074d0c79a5e0cdd13f1924/4-Figure5-1.png)
PDF] An ASIC design for a high speed implementation of the hash function SHA -256 (384, 512) | Semantic Scholar

Whatsminer M30S++ 31W Asic Miner Machine, SHA-256 Algorithm, 104Th/s Hashrate, 3328W Power Consumption, 75Db Noise Level, Ethernet Network Connection Mode | M30S++ 104T Buy, Best Price. Global Shipping.

PDF) An ASIC Design for a High Speed Implementation of the Hash Function SHA -256 (384, 512) | Jerry Wang - Academia.edu
![PDF] An ASIC design for a high speed implementation of the hash function SHA -256 (384, 512) | Semantic Scholar PDF] An ASIC design for a high speed implementation of the hash function SHA -256 (384, 512) | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/60b9bb5952c3870d2f074d0c79a5e0cdd13f1924/3-Figure3-1.png)
PDF] An ASIC design for a high speed implementation of the hash function SHA -256 (384, 512) | Semantic Scholar