Amazon.com: Yubico YubiKey 5C - Two Factor Authentication USB Security Key, Fits USB-C Ports - Protect Your Online Accounts with More Than a Password, FIDO Certified : Electronics
A Click from the Backyard | Analysis of CVE-2020-9332, a Vulnerable USB Redirection Software - SentinelLabs

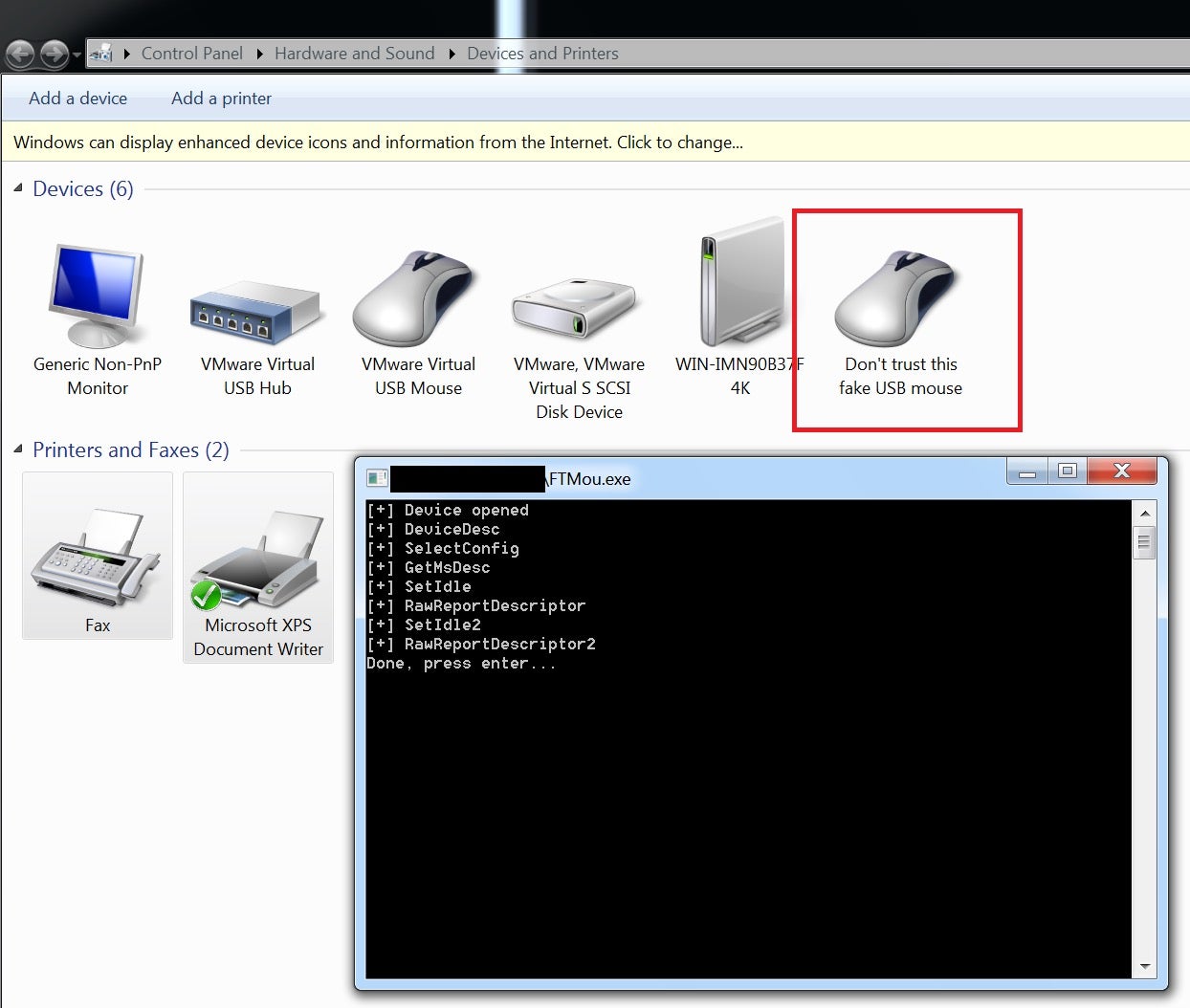
Defending against weaponized hardware: Windows Defender ATP & Microsoft Intune to the rescue! A story about RubberDucky & an evil mouse | by Maarten Goet | Medium